


A Grain of Salt: dealing with Operating Systems security debate
An article (ref: http://www.zone-h.org/winvslinux ) recently released by Zone-h website and containing data updated to May 2003 takes into account the evolution of the number of confirmed defacements (attacks conducted by humans to web servers which leave a trace in the form of modified webpages on the server and are then reported to Zone-h for verification, called also overt attacks) performed by cybercriminals on various server platforms. This study has been taken by many as a demonstration of the superior security of Windows server operating systems in respect to Linux.
Part 1: Overt Attacks
The charts included, taken from that very Zone-h feature, are indeed worth a lot of words.
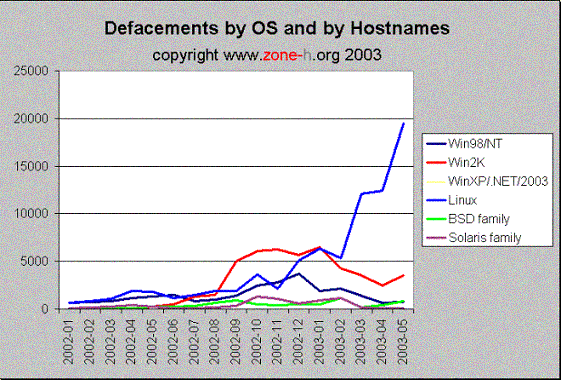
This one shows the evolution of this kind of attack by hostnames. Given the fact that a single webserver can host multiple sites, the chart itself is not valid 'per se' to describe how many machines running Linux or Windows have been successfully attacked by human crackers and 'defaced'. This is easily assessed looking at the following chart:
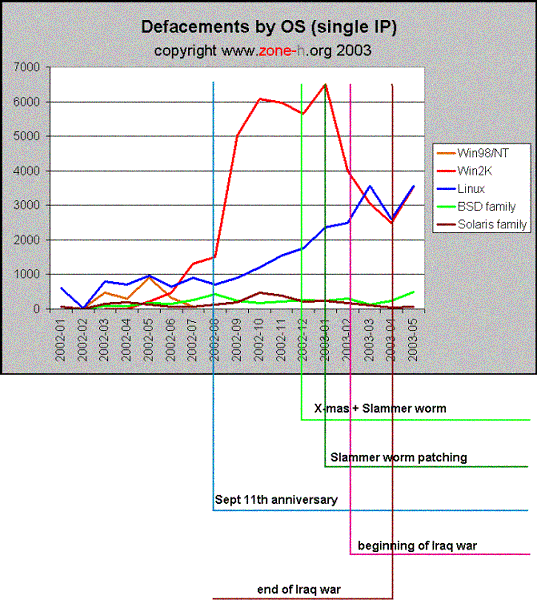
Here the situation appears quite different: the number of actual machines compromised is currently kind of equal for the two OS families, but the recent past shows a peak in damaged machines running Windows. This can lead to a bit of confusion among readers: the two charts seem to be in stark contrast.
This is only partially true: we can guess that an increasing number of providers are using Linux to deploy multiple websites on single webservers, and an attack to a single machine can lead to a so-called mass defacement, which weighs on Linux statistics heavily. Windows machines are also used by ISPs, but it seems that Linux for economic and flexibility reasons is more and more used for this kind of deployments.
An interesting point of the above chart is the correlation shown in the image between the Slammer worm (an automated attack by a malicious program which affected Microsoft SQL Server at the end of 2002) and the increase in Windows defacements. This appears at least strange, because Slammer did not attack IIS webservers (at least directly) and can't be held responsible of web defacements (at least directly). Besides it attacked a number of machines which is estimated much higher than 7000
(ref: http://news.com.com/2009-1001-983540.html?tag=prntfr)
at a lightning speed. So why the patching of Slammer marks a decrease of web defacements? Again we can guess that many sistem administrators, while patching their SQL servers for the Slammer worm have also given a look to their IIS servers and applied security measures (patching, firewalling...) which led to a more normal exploitation susceptibility for the Windows platforms. The big peak in Windows defacements could be due to vulnerabilities which went unpatched for a long time; besides, the Sept.11 anniversary could be also a reason for the general explosion of defacements? Could be, but the effect of an anniversary is not typically lasting for 6-7 months...
The total approximate number of defacements is accessible also through a release of mi2g (ref: http://www.mi2g.com/status ) and show, for 2002 (the last complete year) a number of defacements of about 85000 machines (assuming most probably a count by single IP) with Windows systems accounting for about 49000 attacks and Linux systems accounting for 24000 'overt attacks'.
So what can we conclude from the comparative analysis of this data? Not very much in absence of other data like the actual number of hosts running Linux or Windows on the Internet or the percentage of mass defacements among the two platforms. But also in presence of accessory data like this, we have to take into account a big number of factors, as the money invested by site owners to secure and keep up to date their webservers, the functionalities enabled typically in every platform (ie. Apache with PHP or IIS with ASP) and the ease of patching for every platform.
2. Some automated attacks
In contrast with the human-led defacements, many Internet servers are daily compromised by automated attacks, frequently by worms (malicious code which self-replicates and spreads using known vulnerabilities of host systems).
On July 19, 2001 more than 359,000 computers were infected with the Code-Red (CRv2) worm in less than 14 hours. At the peak of the infection frenzy, more than 2,000 new hosts were infected each minute.
The quote is from the CAIDA website
(ref: http://www.caida.org/analysis/security/code-red )
and is interesting for a comparison between figures of human-led and worm-led attacks. Code Red exploited a flaw in Microsoft IIS webservers.
In the largest such incident since the Code Red and Nimda worms bored into servers in 2001, the Sapphire worm--also known as Slammer and SQLExp--infected more than 120,000 computers(...)
This quote is from News.com website
(ref: http://news.com.com/2100-1001-982135.html?tag=nl ).
The Slammer worm has been held responsible for networks overloads worldwide, all this obtained attacking just a class of Internet connected computers (Microsoft SQL Servers). Strictly speaking this worm did not attack webservers, but it is worth mentioning in the bigger picture of 'server operating systems security' debate. Besides, as noticed before, this worm has been held responsible (not correctly, we guessed) for Windows defacements.
The most recent major outbreak--Nimda, which infected hundreds of thousands of systems in September--was "the ultimate cocktail," a worm that exploited multiple methods of spreading, and attacked systems through multiple security holes in Microsoft's Internet Information Services software(...)
This quote is from the Pcworld.com website
(ref: http://www.pcworld.com/news/article/0,aid,71343,00.asp )
and testifies about another popular worm which targeted Windows mixed platforms back in 2001.
For a comparison, it's worth quoting an article regarding the Slapper worm, taken from the Vnunet website
(ref: http://www.vnunet.com/News/1135137 )
The Internet Storm Centre (ISC), the early warning system from the Sans Institute, is on yellow alert for the first time in months as the Slapper worm continues its infection of Apache web servers. (...) Slapper-infected servers have already been linked to denial of service (DoS) attacks against other machines. It is thought that some script kiddies found the source code for a concept attack known as peer-to-peer UDP Distributed DoS (PUD) on a security site and turned it into a working worm. The ISC has confirmed that around 6,000 servers are currently infected. But speculation on the BugTraq security mailing list suggests that numbers may be as high as 30,000. A patch has already been released by the OpenSSL crew (...).
The Slapper worm exploited vulnerable Apache servers back in 2002.
3. A bigger picture
A first conclusion could be that human attacks are more or less continuous, and reach figures around 100000 yearly, but automated exploits have by far outweighed them, sometimes in days or hours (see examples above). Another key point is that nothing in this 'bigger picture' is testifying a lesser security of Linux operating systems in respect to their Windows counterparts.
This article is not aimed to denigrate Windows or praise Linux OSes, the aim of this paper is to put 'en garde' journalists and end users from the dangers of simplification. If in the desktop arena Windows is by far the most targeted platform (tens of thousands of viruses exist according to some estimations), and countless papers have tried to explain it as a result of poor design or simply of market dominance, in the server arena, where the host can't be 'hidden' completely from attackers, no operating system can be considered 'less targeted', because very skilled humans can penetrate almost any security measure. And if humans don't bother you, automated attacks are always waiting for unpatched software vulnerabilities.
As a final consideration, may we strongly suggest to nonexpert system administrators NOT to run their own webservers (on whatever platform) and let instead run their websites by a good Service Provider? Assistance and disaster recovery are better done by professionals...if, instead, you belong to the Elected Uberadministrators, you sure don't need our advice.
This article is not intended to denigrate/damage any of the quoted websites (may we agree with them or not) or to steal their intellectual property. All sources are properly quoted and the information used for educational purpose only.
21th of July, 2003
Simone Bianchi
UPDATE
In November I contacted the Administrator of Zone-h with the following mail:
Dear
Admin
I already wrote to you from another e-mail address. Assuming my post did
not reach you, I'm reposting to you to request if it's possible to have
the defacement archive also selectable to show single-IP defacements (ie.
show mass defacements as a single hit). Some IT pros would find useful
to know how many machines (and not virtual websites)
have been compromised for each OS. As regarding your useful article of
some months ago (Windows vs. Linux) I've written a comment article I'd
like the author to read.
Here is the address:
http://www.thinkmagazine2.org/versione_layer/security.html
Thanks for your attention
Simone Bianchi
Here is the answer of the Admin:
Dear
Simone, I got hold on your mail and I went to read your article.
The analisys you did is quite right, except for one point, where you said:
"An interesting point of the above chart is the correlation shown
in the image between the Slammer worm (an automated attack by a malicious
program which affected Microsoft SQL Server at the end of 2002) and the
increase in Windows defacements. This appears at least strange, because
Slammer did not attack IIS webservers (at least directly) and can't be
held responsible of web defacements (at least directly). Besides it attacked
a number of
machines which is estimated much higher than 7000"
The correlation you are referring to, is actually the opposite. In the
article we released together with the chart it is stated that the slammerworm
is actually the reason of the DECREMENT of the windows defacement. We
never stated that slammerworm was the cause of the defacements, we rather
stated that the worm and its wide publicity on the media was the cause
that pushed admins to patch, thus rendering their windows systems less
attackable.
Also you wrote:
"the Sept.11 anniversary could be also a reason for the general explosion
of
defacements? Could be, but the effect of an anniversary is not typically
lasting for 6-7 months..."
Being in contact with the defacers panorama since a long time, i can tell
you that those kind of anniversaries are actually lasting more than 6-7
months. In fact, we ecperienced a peak also in the last sept anniversary,
2 years after the tragedy. On the other hand, we do agree with you on
one point:
"So what can we conclude from the comparative analysis of this data?
Not very much in absence of other data like the actual number of hosts
running Linux or Windows on the Internet or the percentage of mass defacements
among the two platforms. But also in presence of accessory data like this,
we have to take into account a big number of factors, as the money invested
by site owners to secure and keep up to date their webservers, the functionalities
enabled typically in every platform (ie. Apache with PHP or IIS with ASP)
and the ease of patching for every platform."
In fact, in my speech at the Defcon 11, I commented those charts with
the same phrase.
I would also add that given the fact that today the attacks are conducted
also on application and database level, there is no sense at all in deciding
if Windows is better than Linux (in security) just judging the raw numbers
of the defacements.
About the request of having the defacement archive also selectable to
show single-IP defacements , we will probably implement it in the next
version of Zone-H.
Regards, SyS64738 www.zone-h.org admin.
UPDATE (2)
Later on, encouraged by the kindness and competence of Admin, I wrote back to him :
Caro
(first name of Sys64738)
(immagino che siamo ambedue italiani)
vorrei pubblicare la tua lettera come commento al mio articolo quando
il tempo me lo permetterà...
spero che tu non abbia nulla in contrario.
(NOTE: I've reason to think Admin is Italian, so I'm telling him in Italian I'd like to publish these letters in an article.)
Besides
(getting back to English) if you agree with the publication of this letter,
I'd like to ask you an opinion about malware in Windows and Linux server
worlds.
Doing a bit of research on the Net it's easy to discover how the first http worms were born and spread on Unix platforms. Nevertheless in the recent past the worst Unix worms (ie. Slapper) spread in a rather confined way, in respect to lightnings as Slammer (curious name resemblance) or Code Red or also Nimda. And this all in spite of the Apache/Linux/BSD http server panorama dominance...
Is it, according to you, due to the fact Windows systems are often deployed
more or less equal to one another, while their opensource counterparts
are a more varied panorama, rendering them less targetable by automatic
exploits (but NOT by humans, which are *sigh* more versatile)?
Or were rather Windows servers targeted using the weaknesses of the Win95/98
desktops (as in the case of Nimda)?
Grazie
per l'attenzione, non mancare di avvertirmi se neghi il consenso alla
pubblicazione.
La rivista l'avrai già guardata, ti posso dire che le contribuzioni
sono sempre state di qualità, quindi la tua voce è in buone
mani.
(NOTE:I'm asking him in Italian to deny explicitly his allowance to publish if he doesn't want me to. I'm also praising Tmag ;-))
Ciao
Simone
_____________________
As soon as I'll receive a follow-up I'll publish it.
Meanwhile, if Sys64738 did not receive the e-mail or was unable to comment for whatever reason (btw. I switched mail provider in this period, though leaving pointers to reach me safely), please send mail to thinkmagazine@simonebianchi.net . I'm always available (within reasonable time, after which Tmag articles go out-of-maintenance) for further updates to this page.
3rd of December, 2003
Simone Bianchi
Updated: February 2008 (mail address)